While the snowball of big data is rushing down a mountain gaining speed and volume, companies are trying to keep up with it. And down they go, completely forgetting to put on masks, helmets, gloves and sometimes even skis. Without these, it’s terribly easy to never make it down in one piece. And putting on all the precaution measures at a high speed can be too late or too difficult.
Prioritizing big data security low and putting it off till later stages of big data adoption projects isn’t always a smart move. People don’t say “Security’s first” for no reason. At the same time, we admit that ensuring big data security comes with its concerns and challenges, which is why it is more than helpful to get acquainted with them.
And as ‘surprising’ as it is, almost all security challenges of big data stem from the fact that it is big. Very big.
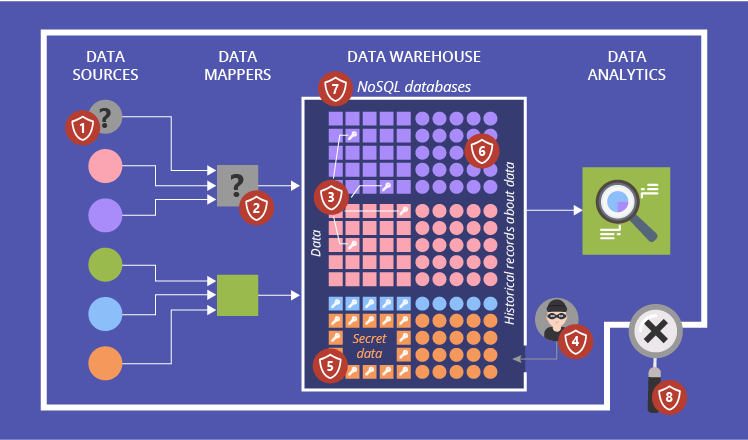
Short overview
Problems with security pose serious threats to any system, which is why it’s crucial to know your gaps. Here, our big data experts cover the most vicious security challenges that big data has in stock:
- Vulnerability to fake data generation
- Potential presence of untrusted mappers
- Troubles of cryptographic protection
- Possibility of sensitive information mining
- Struggles of granular access control
- Data provenance difficulties
- High speed of NoSQL databases’ evolution and lack of security focus
- Absent security audits
Now that we’ve outlined the basic problem areas of big data security, let’s look at each of them a bit closer.
#1. Vulnerability to fake data generation
Before proceeding to all the operational security challenges of big data, we should mention the concerns of fake data generation. To deliberately undermine the quality of your big data analysis, cybercriminals can fabricate data and ‘pour’ it into your data lake. For instance, if your manufacturing company uses sensor data to detect malfunctioning production processes, cybercriminals can penetrate your system and make your sensors show fake results, say, wrong temperatures. This way, you can fail to notice alarming trends and miss the opportunity to solve problems before serious damage is caused. Such challenges can be solved through applying fraud detection approach.
#2. Potential presence of untrusted mappers
Once your big data is collected, it undergoes parallel processing. One of the methods used here is MapReduce paradigm. When the data is split into numerous bulks, a mapper processes them and allocates to particular storage options. If an outsider has access to your mappers’ code, they can change the settings of the existing mappers or add ‘alien’ ones. This way, your data processing can be effectively ruined: cybercriminals can make mappers produce inadequate lists of key/value pairs. Which is why the results brought up by the Reduce process will be faulty. Besides, outsiders can get access to sensitive information.
The problem here is that getting such access may not be too difficult since generally big data technologies don’t provide an additional security layer to protect data. They usually tend to rely on perimeter security systems. But if those are faulty, your big data becomes a low hanging fruit.
#3. Troubles of cryptographic protection
Although encryption is a well-known way of protecting sensitive information, it is further on our list of big data security issues. Despite the possibility to encrypt big data and the essentiality of doing so, this security measure is often ignored. Sensitive data is generally stored in the cloud without any encrypted protection. And the reason for acting so recklessly is simple: constant encryptions and decryptions of huge data chunks slow things down, which entails the loss of big data’s initial advantage – speed.
#4. Possibility of sensitive information mining
Perimeter-based security is typically used for big data protection. It means that all ‘points of entry and exit’ are secured. But what IT specialists do inside your system remains a mystery.
Such a lack of control within your big data solution may let your corrupt IT specialists or evil business rivals mine unprotected data and sell it for their own benefit. Your company, in its turn, can incur huge losses, if such information is connected with new product/service launch, company’s financial operations or users’ personal information.
Here, data can be better protected by adding extra perimeters. Also, your system’s security could benefit from anonymization. If somebody gets personal data of your users with absent names, addresses and telephones, they can do practically no harm.
#5. Struggles of granular access control
Sometimes, data items fall under restrictions and practically no users can see the secret info in them, like, personal information in medical records (name, email, blood sugar, etc.). But some parts of such items (free of ‘harsh’ restrictions) could theoretically be helpful for users with no access to the secret parts, say, for medical researchers. Nevertheless, all the useful contents are hidden from them. And this is where talk of granular access starts. Using that, people can access needed data sets but can view only the info they are allowed to see.
The trick is that in big data such access is difficult to grant and control simply because big data technologies aren’t initially designed to do so. Generally, as a way out, the parts of needed data sets, that users have right to see, are copied to a separate big data warehouse and provided to particular user groups as a new ‘whole’. For a medical research, for instance, only the medical info (without the names, addresses and so on) gets copied. Though, the volumes of your big data grow even faster this way. Other complex solutions of granular access issues can also adversely affect the system’s performance and maintenance.
#6. Data provenance difficulties
Data provenance – or historical records about your data – complicates matters even more. Since its job is to document the source of data and all manipulations performed with it, we can only image what a gigantic collection of metadata that can be. Big data isn’t small in volume itself. And now picture that every data item it contains has detailed information about its origin and the ways it was influenced (which is difficult to get in the first place).
For now, data provenance is a broad big data concern. From security perspective, it is crucial because:
- Unauthorized changes in metadata can lead you to the wrong data sets, which will make it difficult to find needed information.
- Untraceable data sources can be a huge impediment to finding the roots of security breaches and fake data generation cases.
#7. High speed of NoSQL databases’ evolution and lack of security focus
This point may seem as a positive one, while it actually is a serious concern. Now NoSQL databases are a popular trend in big data science. And its popularity is exactly what causes problems.
Technically, NoSQL databases are continuously being honed with new features. And just like we said in the beginning of this article, security is being mistreated and left in the background. It is universally hoped that the security of big data solutions will be provided externally. But rather often it is ignored even on that level.
#8. Absent security audits
Big data security audits help companies gain awareness of their security gaps. And although it is advised to perform them on a regular basis, this recommendation is rarely met in reality. Working with big data has enough challenges and concerns as it is, and an audit would only add to the list. Besides, the lack of time, resources, qualified personnel or clarity in business-side security requirements makes such audits even more unrealistic.
But don’t be scared: they are all solvable
Yes, there are lots of big data security issues and concerns. And yes, they can be quite crucial. But it doesn’t mean that you should immediately curse big data as a concept and never cross paths with it again. No. The thing you should do is carefully design your big data adoption plan remembering to put security to the place it deserves – first. This may be a tricky thing to do, but you can always resort to professional big data consulting to create the solution you need.
Big data is another step to your business success. We will help you to adopt an advanced approach to big data to unleash its full potential.

