
New Phishing Campaign Targets iPhone Users in India with India Post Lures
The FortiGuard Labs Threat Research team recently observed a number of social media posts commenting on a fraud campaign targeting India Post users. India Post is India’s government-operated postal system. It is part of the Ministry of Communications and has a vast network of over 150,000 post offices across the country, making it one of the largest postal systems in the world.
In this campaign, iPhone users are being targeted by smishing attacks that claim to be from India Post. The scam involves sending an iMessage to iPhone users, falsely claiming that a package is waiting at an India Post warehouse.
Public reporting suggests this campaign is being attributed to a China-based threat actor known as the Smishing Triad. This group has previously targeted other regions, including the US, UK, EU, UAE, KSA, and, most recently, Pakistan.
Modus-Operandi
The threat actors begin by sending a message via iMessage directly to the recipients’ registered Apple ID email addresses. The sender ID could be a newly registered Apple ID or a compromised account. This method ensures that the message appears within the recipient’s Messages app as an iMessage, distinct from traditional email communications, provided both parties use iMessage-enabled devices and have their Apple IDs configured for iMessage.
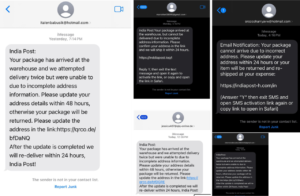

Figure 1. Smishing lures sent to users in India. Screenshots collected from social media posts.
Once the user clicks the link in the message, they are directed to a fraudulent website that mimics the official India Post site. Here, they are asked to provide personal information, including their name, address, email ID, and phone number. The site then requests debit or credit card details for a supposed redelivery fee of INR 25.02, leading to potential financial theft and further exploitation of the collected data.
Fraudulent Domain Registrations and Hosting
FortiGuard Labs discovered the phishing domain ‘indiapost[.]top,’ which impersonates India Post through a cloned copy of the original website. The domain itself does not host any content; instead, specific paths on the domain are utilized to host the phishing website.
Between January and July 2024, over 470 domains were registered to impersonate India Post, with a significant number (296) registered through a Chinese registrar, Beijing Lanhai Jiye Technology Co., Ltd. This high concentration of registrations through a Chinese registrar raises concerns about the intentions behind these activities. The top-level domains (TLDs) frequently used include ‘vip,’ ‘top,’ and ‘buzz,’ with registration costs varying from USD 1 to USD 5 per domain.
The investment in domain registrations alone exceeds USD 1,500, highlighting the scale and commitment of the phishing operation. This financial outlay, combined with hosting and development costs, underscores the significant threat posed by these scams. The campaign’s scale suggests that numerous victims are likely to fall prey, resulting in substantial financial losses and data breaches.
Supporting Quote:
“Phishing scams are becoming increasingly sophisticated, making it essential for everyone to stay vigilant and take proactive steps to protect themselves,” says Vishak Raman, Vice President of Sales, India, SAARC, SEA & ANZ at Fortinet. “To stay safe, always verify the authenticity of any unexpected messages and avoid sharing personal information through email or messaging apps. Use strong, unique passwords and enable multi-factor authentication on your accounts. Keeping your software updated and staying informed about the latest phishing tactics are also crucial.”
“Business also must train employees to recognize and respond to phishing threats. For organizations, our FortiPhish Phishing Simulation Service uses real-world simulations to help test user awareness and vigilance, training and reinforcing proper practices when users encounter targeted phishing attacks. By following these high-level recommendations, you can significantly reduce the risk of falling victim to these malicious schemes.”
For a detailed analysis and report read the blog.