Computers separate the OS into two modes for resource allocation and security purposes.
The distinction protects a computer system’s basic functionality and ensures stability. While the computer is operating, it separates more abstract functions from those that involve the computer’s essential components to improve fault tolerance.
The computer’s CPU switches between user and kernel mode depending on the code that’s running. Certain applications are restricted to user mode, while others operate in kernel mode. Generally, user applications operate in user mode, whereas basic OS components function in kernel mode.
The 2024 CrowdStrike outage, which rendered millions of Windows machines inoperable, was precipitated by security software that malfunctioned while running in kernel mode.
What is user mode?
User mode is an OS state with restricted access to the computer system’s hardware and resources. User mode has a lower level of privileges than kernel mode and cannot execute specific commands that have the potential to interfere with the stability of the system. Applications in user mode can only interact with privileged hardware and perform privileged operations through a system call, which is transmitted using the OS’ API.
User applications, such as word processors, web browsers and video players, run in user mode. When a user launches one of these applications, the OS creates a process that gives the application its own private virtual address space in memory.
This gives programs in user mode a private section of memory that other applications cannot access and keeps applications in user mode from altering each other’s data. In this mode, if one application crashes, it doesn’t take the entire system down with it because it runs in isolation from other applications.
What is kernel mode?
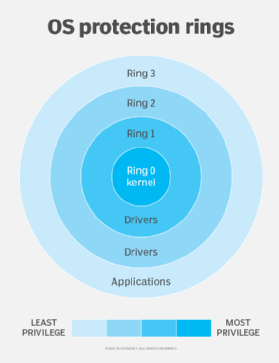
Kernel mode is an OS state with unrestricted access to system resources and hardware. It is a privileged mode where the OS’ core functions are conducted. Kernel mode enforces isolation processes by handling system calls from user mode. It also has direct access to peripheral devices.
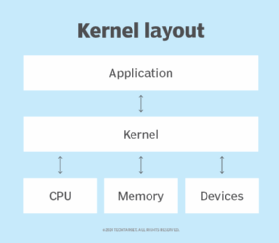
In kernel mode, there is no separation of virtual address space — all code in this mode shares the same virtual address space in memory. This means the CPU can switch between running programs and reading and writing both kernel memory and user memory.
Programs that run in kernel mode include the OS itself, process-related code and some security software. Program data running in this mode is not protected from other applications. If an application crashes in kernel mode, it can negatively affect the other applications running in kernel mode. For example, if a driver crashes in kernel mode, it could potentially corrupt the entire OS.
User mode vs. kernel mode
User and kernel mode are two OS states that work together to ensure the security and stability of computer systems.
| Characteristics | User mode | Kernel mode |
| Definition | Restricted OS mode for running application code | Privileged mode for core OS functions |
| Resource access | Limited access to system resources and hardware | Full access to system resources and hardware |
| Memory access | Cannot access kernel memory directly; code is isolated | Unrestricted access to user and kernel memory; code is not isolated |
| Privilege level | Lower privilege level | Higher privilege level |
| Purpose | Runs nonsystem software, like applications | Manages system resources and enforces restrictions |
| Security and stability | Less critical for operations and less consequence for errors | Critical for system operations but larger consequence for errors |
How user mode and kernel mode work together
The CPU contains a register that notes the mode that the CPU is in — either user mode or kernel mode. The CPU boots up in kernel mode and then loads and runs the OS. Eventually — on a trigger from the user, for example — the OS loads the instructions for a program to run and sets up memory for the program to run. Before executing the instructions, the CPU changes the register to denote that the CPU is in user mode. Then, the CPU executes the program in user mode, where it has a safe level of restrictions.
How to switch from user mode to kernel mode
User mode applications are generally restricted from critical system resources but need to access those resources in some contexts. For example, when a program needs to access a hardware device or update system settings, that program performs a system call that indicates the specific service it requires from the kernel. System call instructions have memory protections that make them unmodifiable or readable by user mode programs. After the system call, the CPU is reset back to user mode.
Which programs run in user mode and kernel mode?
Any program that performs memory management, process management or I/O management typically runs in kernel mode. Any software in this mode has full access to the system and thus needs to be trusted. Once running, the code in the kernel or new code that is inserted in the kernel needs to be trusted so that it doesn’t corrupt the core functions of the computer.
System calls establish this trust. Although applications such as word processors are executed in user mode, they use system calls regularly to enter kernel mode and perform processes involving peripherals and memory. For example, if the word processor needs to save a file, it needs to do so through a system call because it needs to write bytes to the disk. The same goes for typing or moving the cursor — the program needs to interact with the hardware in some way and needs some kernel-level access to do so.
Another example of a system call occurs when a program is listening for incoming network connections. The system call tells the kernel’s networking stack to arrange data structures to prepare it to receive future incoming network packets.
The above are examples of programs that execute in user mode but use system calls to access kernel mode. Another example of software that requires access to the kernel is third-party security software. One notable example of this is CrowdStrike’s Falcon sensor, which regularly publishes content updates to the kernel to help the software detect new threats. The sensor validates the content, which allows it, theoretically, to do its job safely in the kernel.
However, because of a bug in the content validator, a content update passed through with problematic data. This caused the CrowdStrike software to crash. Because the software — at least part of it — resided in the kernel, the Windows machines that received the update completely crashed as well. This example speaks to the importance of only running trusted processes in the kernel.
Ben Lutkevich is site editor for TechTarget Software Quality. Previously, he wrote definitions and features for Whatis.com.

